Cybersecurity researchers have discovered a case of "forced authentication" that could be exploited to leak a Windows user's NT LAN Manager (NTLM) tokens by tricking a victim into opening a specially crafted Microsoft Access file.
The attack takes advantage of a legitimate feature in the database management system solution that allows users to link to external data sources, such as a remote SQL Server table.
"This feature can be abused by attackers to automatically leak the Windows user's NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80," Check Point security researcher Haifei Li said. "The attack can be launched as long as the victim opens an .accdb or .mdb file. In fact, any more-common Office file type (such as a .rtf ) can work as well."
NTLM, an authentication protocol introduced by Microsoft in 1993, is a challenge-response protocol that's used to authenticate users during sign-in. Over the years, it has been found to be vulnerable to brute-force, pass-the-hash, and relay attacks.
The latest attack, in a nutshell, abuses the linked table feature in Access to leak the NTLM hashes to an actor-controlled server by embedding an .accdb file with a remote SQL Server database link inside of an MS Word document using a mechanism called Object Linking and Embedding (OLE).
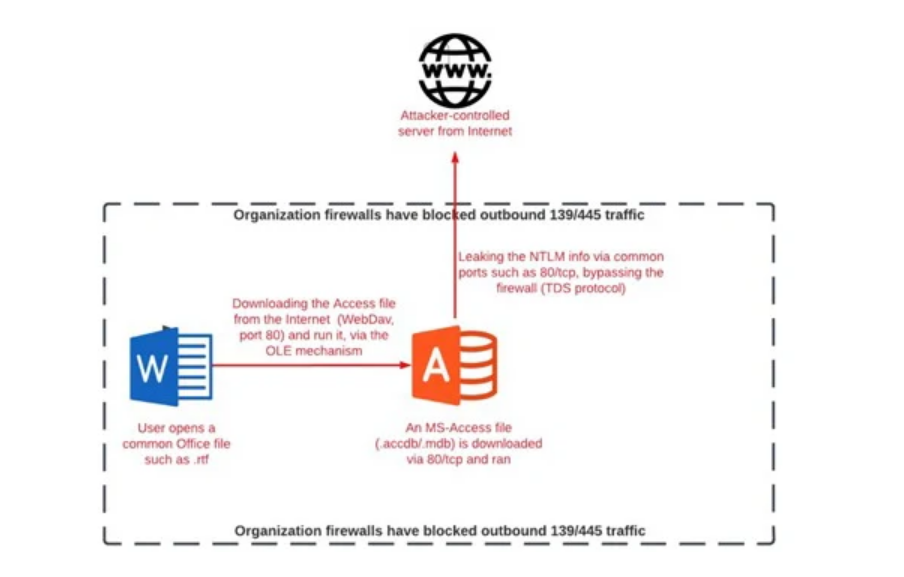
"An attacker can set up a server that they control, listening on port 80, and put its IP address in the above 'server alias' field," Li explained. "Then they can send the database file, including the linked table, to the victim."
Should the victim open the file and click the linked table, the victim client contacts the attacker-controlled server for authentication, enabling the latter to pull off a relay attack by launching an authentication process with a targeted NTLM server in the same organization.
The rogue server then receives the challenge, passes it on to the victim as part of the authentication process, and gets a valid response, which is ultimately transmitted to the NTLM server.
While Microsoft has since released mitigations for the problem in the Office/Access version (Current Channel, version 2306, build 16529.20182) following responsible disclosure in January 2023, 0patch has released unofficial fixes for Office 2010, Office 2013, Office 2016, Office 2019, and Office 365.
The development also comes as Microsoft announced plans to discontinue NTLM in Windows 11 in favor of Kerberos for improved security.