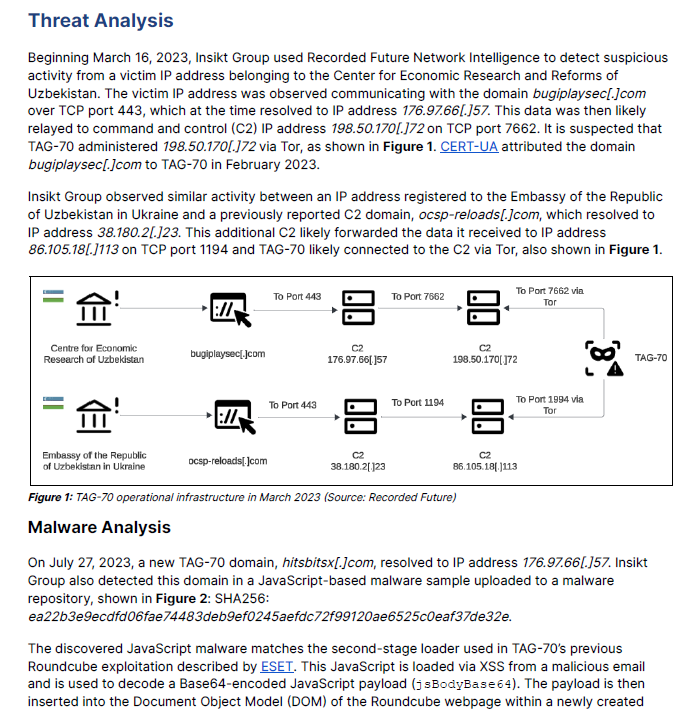
Extortion, increasingly high ransom demands and sensitive data leaks continued in the second half of 2021, impacting organizations such as Kaseya and MediaMarkt.
Ransomware attacks showed no sign of slowing down in 2021 as enterprises continued to fall victim to data theft and the forced shutdown of operations.
During the first half of 2021, attacks struck critical infrastructure organizations and government agencies, causing significant fallout. Ransomware gangs targeted larger organizations with increasingly large ransom demands.
Those trends continued, and no sector was left unturned in the second half of 2021, including cryptocurrency exchanges. Extortion remained a key tactic for ransomware groups and in many cases, data leak sites called attention to attacks even before companies disclosed the incidents. Attackers appeared to follow through on many of those threats by exposing sensitive files.
Here are 10 of the biggest ransomware attacks for the second half of the year as 2021 comes to a close.
1. Kaseya
On July 2, Kaseya suffered a supply chain attack when REvil operators hit the vendor that provides remote management software for managed service providers (MSPs). In a statement to its website, Kaseya attributed the attack to the exploitation of zero-day vulnerabilities in the on-premises version of its VSA product. The flaws allowed attackers to bypass authentication and use VSA to remotely send arbitrary commands, leading to the deployment of ransomware on MSPs’ clients. The broad nature of the incident garnered the attention of the FBI, which issued an incident response guide.
As of July, Kaseya said it was “aware of fewer than 60 customers” impacted by the attack, but the fallout reached “1,500 downstream businesses.” In an incident update on July 22, Kaseya said it “obtained a universal decryptor key” from a third party and that it was working to remediate impacted customers. It turned out the third party was not REvil, as Kaseya confirmed it did not negotiate with the attackers and “in no uncertain terms” did not pay a ransom to obtain the tool.
2. Accenture
Global consulting firm Accenture confirmed it suffered a ransomware attack in August, though at the time the company said there was “no impact” on operations or on clients’ systems. LockBit operators claimed responsibility for the attack and set a countdown to leak the stolen data to their public leak site if a ransom was not paid. In the statement to SearchSecurity, Accenture said it “immediately contained the matter and isolated the affected servers” and fully restored affected systems from backups. However, in an SEC filing in October, Accenture disclosed that some client systems were breached, and attackers stole and leaked proprietary company data.
3. Ferrara Candy Company
This attack made the list for its unfortunate timing, as the candy corn manufacturer was hit right before Halloween. Ferrara disclosed to media outlets that it was hit by a ransomware attack on Oct. 9 and was working with law enforcement in an investigation, as well as with a technical team to “restore impacted systems.” While productivity was impacted, as of Oct. 22 work had resumed in “select manufacturing facilities” and shipping operations were almost back to normal, according to the company. Ferrara did not disclose the type of ransomware or reveal if a ransom was paid in order to resume operations.
4. Sinclair Broadcast Group
On October 16, an investigation into a potential security incident against Sinclair Broadcast Group revealed the media conglomerate had suffered a ransomware attack and data breach. Subsequently, Sinclair contacted a cybersecurity forensic firm and notified law enforcement along with other government agencies. While the type of ransomware, the extent of stolen data and whether a ransom was paid remain unclear, the attack caused disruptions to “certain office and operational networks.” That disruption included some Sinclair-owned broadcast networks that experienced technical difficulties related to the ransomware attack and were temporarily unable to broadcast. As of a statement on October 18, Sinclair said it “cannot determine” the attack’s “material impact on its business, operations or financial results.”
5. Eberspächer Group
A ransomware attack against the international automotive supplier caused extended downtime at production plants and, according to reports, forced paid time off for the some of the factory workforce. In a statement to its website, Eberspächer Group, which operates 50 plants, said it was the victim of a ransomware attack on Oct. 24 that impacted part of its IT infrastructure. Authorities were contacted and precautionary measures were taken to shut down all IT systems and disconnect the network. Updates posted to Twitter showed Eberspächer’s website was offline through Nov. 29, more than one month later. However, “most plants worldwide” were delivering as of Nov. 5, when Eberspaecher tweeted that it was “on the right track.”
6. National Rifle Association
At the end of October, reports surfaced that the National Rifle Association (NRA) was the victim of a ransomware attack after Grief ransomware operators posted alleged confidential data to its public leak site. While the NRA did not confirm the ransomware attack or issue a public statement, it did respond on Twitter. Andrew Arulanandam, managing director of NRA public affairs, said the “NRA does not discuss matters relating to its physical or electronic security.” It’s unclear what the ransom demand was, or whether the nonprofit organization paid it.
7. BTC-Alpha
In a statement to SearchSecurity, cryptocurrency platform BTC-Alpha confirmed it was the victim of a ransomware attack at the beginning of November, right around its five-year anniversary. While it appears no funds were impacted, the attack did take down BTC-Alpha’s website, as well as its app, which remained out of commission through Nov. 20. Initially, a screenshot posted to Twitter by threat intelligence firm DarkTracer sparked rumors of an attack against the cryptocurrency exchange. According to the screenshot, LockBit claimed to have encrypted BTC-Alpha’s data, a common tactic employed by ransomware gangs to pressure victims into paying. BTC-Alpha founder and CEO Vitalii Bodnar has since attributed the attack to a competitor and said he “doubts the attack was related to LockBit,” but could not share more information as the investigation was still underway.
8. MediaMarkt
MediaMarkt made the list for both its size — over 1,000 electronic retail stores in Europe and over 50,000 employees — as well as the significant amount of the alleged demand made in this ransomware attack. A report by Bleeping Computer on Nov. 8 said the demand was $240 million and attributed it to the Hive ransomware group. Cybersecurity company Group-IB detailed Hive’s activity and found the ransomware-as-a-service group claimed hundreds of victims in just six months. According to Group-IB, it took Hive less than half a year to break the record for highest ransom demand. While MediaMarkt confirmed to Bleeping Computer that a cyber attack took place, it’s unclear when the company’s operations were fully restored and whether a ransom payment was made.
9. Superior Plus
Natural gas supplier Superior Plus Corp. confirmed it was the victim of a ransomware attack that occurred on Dec. 12. In a statement on Dec. 14, the Canada-based corporation said it “temporarily disabled certain computer systems and applications” in the wake of an investigation and “is in the process of bringing these systems back online.” Independent cybersecurity experts were hired to assist in the investigation. At the time of the statement, Superior Plus said it had “no evidence that the safety or security of any customer or other personal data had been compromised.” Superior Plus became the latest energy company to suffer a ransomware attacks, following the high-profile and disruptive attack on Colonial Pipeline Company earlier this year.
10. Kronos
On Dec. 11, Kronos Incorporated spotted unusual activity in its private cloud that included encrypted servers. Two days later, the workforce management provider notified customers that it was the victim of a ransomware attack. In fairly detailed updates provided to its website, Kronos said in response it shut down more than “18,000 physical and virtual systems, reset passwords and disabled VPN site-to-site connections on the UKG side.” The incident impacted Kronos Private Cloud, Workforce Central, Telestaff, Healthcare Extensions and UKG scheduling and workforce management for banks. One significant concern was the ransomware attack’s impact on employee paychecks, since the HR systems provider is widely known for its payroll and time management systems. Last updated on Monday, Kronos said “due to the nature of the incident, it may take up to several weeks to fully restore system availability.”