Vulnerabilities
Vulnerability is a weakness in an IT system that can be exploited by an attacker to deliver a successful attack. They can occur through flaws, features or user error, and attackers will look to exploit any of them, often combining one or more, to achieve their end goal.


Cloud AI Security Alert: Meta's Llama Flaw Leaves Systems Vulnerable to Attack
"Affected versions of meta-llama are vulnerable to deserialization of untrusted data, meaning that an attacker can execute arbitrary code by sending malicious data that is deserialized," Oligo Security researcher Avi Lumelsky said in an analysis earlier this week.
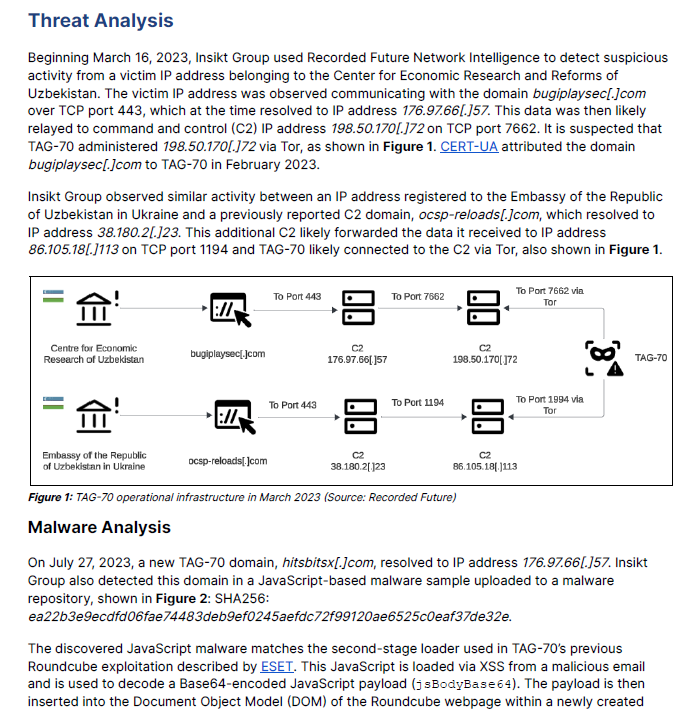
TAG-70 Cyber Espionage Alert: Belarus and Russia-Aligned Hackers Target Email Servers
Exploitation of Roundcube Vulnerabilities: A Persistent Threat
CISA Alerts: Rising Threat of Akira Ransomware Targeting Cisco ASA/FTD Security Flaw
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched security flaw impacting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD)

UPDATE: 'Forced Authentication' to Steal Windows NTLM Tokens
"This feature can be abused by attackers to automatically leak the Windows user's NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80" ...
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild.

New Python malware backdoors VMware ESXi servers for remote access
The new python backdoor adds seven lines inside "/etc/rc.local.d/local.sh," one of the few ESXi files that survive between reboots and is executed at startup.
VMware Beware: Lockbit 3.0 Targeting ESXi hash: 0f7c10dfa562adf15f1f6078ecaee788
Per Twitter @Unit42_Intel a LockBit 3.0 variant using ESXi Locker version 1.2 continues targeting ESXi hash: 0f7c10dfa562adf15f1f6078ecaee788.