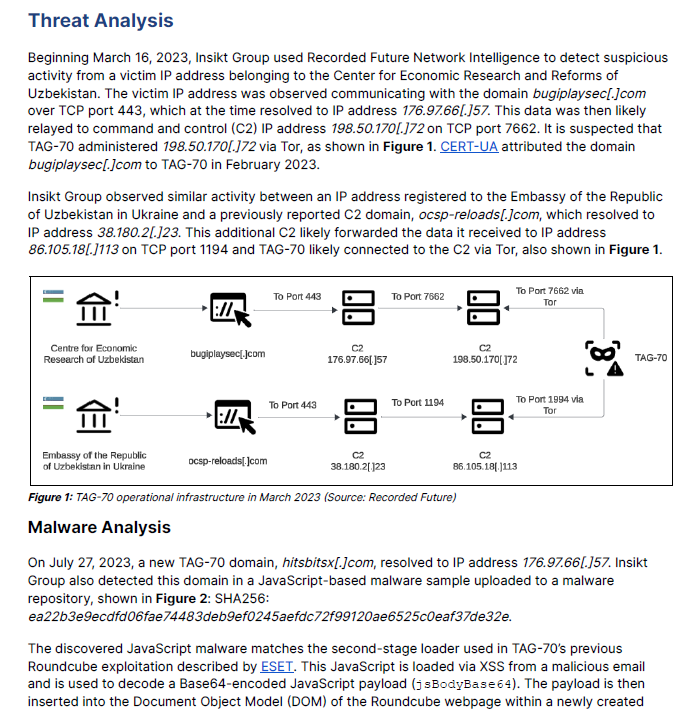
TAG-70 Cyber Espionage Alert: Belarus and Russia-Aligned Hackers Target Email Servers
Exploitation of Roundcube Vulnerabilities: A Persistent Threat
Actions taken through the use of computer networks to disrupt, deny, degrade, or destroy information resident in computers and computer networks, or the computers and networks themselves.
Exploitation of Roundcube Vulnerabilities: A Persistent Threat
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched security flaw impacting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD)
"This feature can be abused by attackers to automatically leak the Windows user's NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80" ...
The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter.
The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies...
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute ..
The reward offer, first reported by WIRED, is also notable for the fact that it marks the first time the face of a Conti associate, known as "Target," has been unmasked. The four other associates have been referred to as "Tramp," "Dandis," "Professor," and "Reshaev."
The company revealed that the attackers could only harvest and steal non-sensitive data from a Box folder linked to a compromised employee's account.