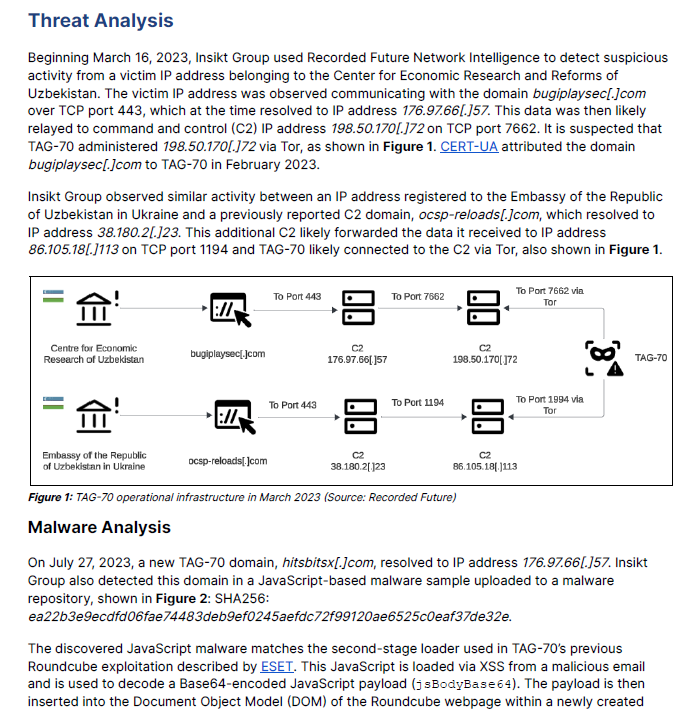
HOWTO: CVE-2021-44228 – (87081) : vCenter Server 6.0/6.5/6.7/7.0 remediation instructions.
https://kb.vmware.com/s/article/87081
CVE-2021-44228 has been determined to impact vCenter Server 7.0.x, vCenter 6.7.x & vCenter 6.5.x via the Apache Log4j open source component it ships.
This vulnerability and its impact on VMware products are documented in the following VMware Security Advisory (VMSA), please review this document before continuing:
- CVE-2021-44228 – VMSA-2021-0028
Highlighted sections indicate the most recent updates. See the Change log at the end of this article for all changes and subscribe the article for updates.
- VCHA needs to be removed before executing the steps in this KB article.
- Environments with external PSCs need to have the steps taken on both vCenter and PSC appliances.
Upgrades documented in the aforementioned advisory should be applied to remediate CVE-2021-44228 when available.
Python script to automate the workaround steps of VMSA-2021-0028 vulnerability on vCenter Server Appliance (Recommended)
To manually apply the workaround for CVE-2021-44228 to vCenter Server Appliance 7.x and 6.x, skip to the relevant sections below:
Click here for vCenter Server Appliance 7.0.x workaround
Click here for vCenter Server Appliance 6.7.x workaround