While such a large uptick may cause alarm, Google puts a positive spin on the news.
“We believe the large uptick in in-the-wild 0-days in 2021 is due to increased detection and disclosure of these 0-days, rather than simply increased usage of 0-day exploits,” wrote Maddie Stone, Project Zero Security Researcher at Google.
Google also notes that – of the 58 zero-day exploits it found in 2021 – just two “stood out as novel: one for the technical sophistication of its exploit and the other for its use of logic bugs to escape the sandbox.”
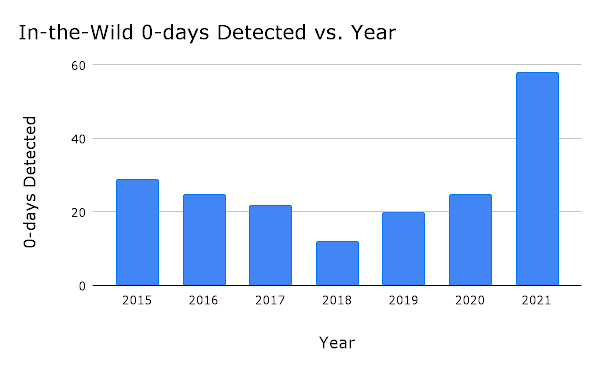
The remaining 56 zero-day exploits were similar to previous and publicly-known vulnerabilities.
However, that’s no reason to become complacent. We’ve seen numerous large attacks using zero-day vulnerabilities over the past couple of years.
“2021 highlighted just how important it is to stay relentless in our pursuit to make it harder for attackers to exploit users with 0-days,” adds Stone.
“We heard over and over and over about how governments were targeting journalists, minoritized populations, politicians, human rights defenders, and even security researchers around the world.”
Last year, Microsoft warned of zero-day vulnerabilities in Windows 10, Exchange, Office, and more—ultimately issuing patches for over 100 potential risks. Apple’s platforms haven’t been spared either, over the past few months alone it’s had to rush out multiple updates to patch various zero-day exploits.
We may never achieve zero zero-day exploits, but faster discovery and patching is the next best thing.
“We want it to be more costly, more resource-intensive, and overall more difficult for attackers to use 0-day capabilities,” Stone summarises.
From Google Project Zero Article:
The More You Know, The More You Know You Don’t Know
A Year in Review of 0-days Used In-the-Wild in 2021

Conclusion
Looking back on 2021, what comes to mind is “baby steps”. We can see clear industry improvement in the detection and disclosure of 0-day exploits. But the better detection and disclosure has highlighted other opportunities for progress. As an industry we’re not making 0-day hard. Attackers are having success using vulnerabilities similar to what we’ve seen previously and in components that have previously been discussed as attack surfaces. The goal is to force attackers to start from scratch each time we detect one of their exploits: they’re forced to discover a whole new vulnerability, they have to invest the time in learning and analyzing a new attack surface, they must develop a brand new exploitation method. And while we made distinct progress in detection and disclosure it has shown us areas where that can continue to improve.
While this all may seem daunting, the promising part is that we’ve done it before: we have made clear progress on previously daunting goals. In 2019, we discussed the large detection deficit for 0-day exploits and 2 years later more than double were detected and disclosed. So while there is still plenty more work to do, it’s a tractable problem. There are concrete steps that the tech and security industries can take to make it even more progress:
- Make it an industry standard behavior for all vendors to publicly disclose when there is evidence to suggest that a vulnerability in their product is being exploited,
- Vendors and security researchers sharing exploit samples or detailed descriptions of the exploit techniques.
- Continued concerted efforts on reducing memory corruption vulnerabilities or rendering them unexploitable.
Through 2021 we continually saw the real world impacts of the use of 0-day exploits against users and entities. Amnesty International, the Citizen Lab, and others highlighted over and over how governments were using commercial surveillance products against journalists, human rights defenders, and government officials. We saw many enterprises scrambling to remediate and protect themselves from the Exchange Server 0-days. And we even learned of peer security researchers being targeted by North Korean government hackers. While the majority of people on the planet do not need to worry about their own personal risk of being targeted with 0-days, 0-day exploitation still affects us all. These 0-days tend to have an outsized impact on society so we need to continue doing whatever we can to make it harder for attackers to be successful in these attacks.
2021 showed us we’re on the right track and making progress, but there’s plenty more to be done to make 0-day hard.