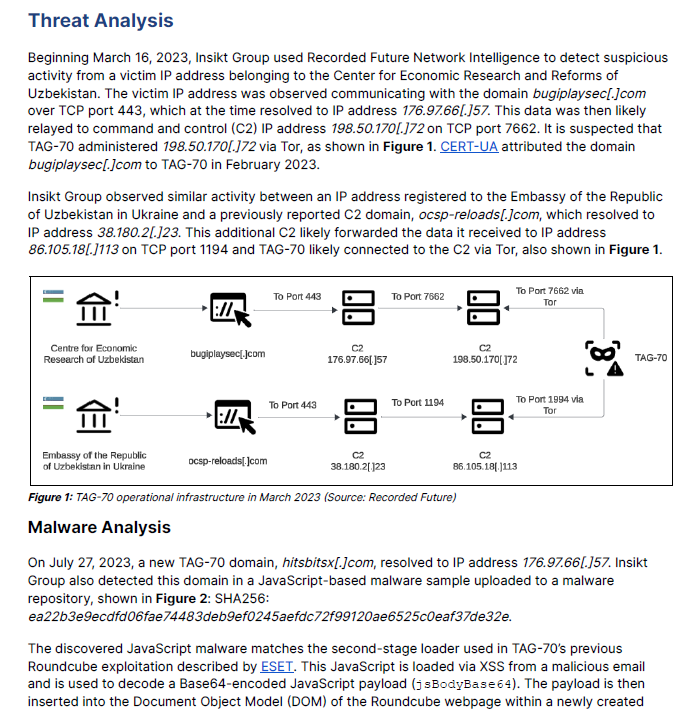
Recent Cybersecurity News from CISA includes threats against critical United States infrastructure by Russian interests. This news released when tension has markedly escalated between U.S. and Russian interests over Ukraine and Kazakhstan.
American cybersecurity and intelligence agencies on Tuesday 1/12/22 released a joint advisory on how to detect, respond to, and mitigate cyberattacks orchestrated by Russian state-sponsored actors.
Per CISA these mitigation efforts below will help cybersecurity professionals and organizations improve their functional resilience by reducing the risk of compromise or severe business degradation.
-
Be prepared. Confirm reporting processes and minimize personnel gaps in IT/OT security coverage. Create, maintain, and exercise a cyber incident response plan, resilience plan, and continuity of operations plan so that critical functions and operations can be kept running if technology systems are disrupted or need to be taken offline.
-
Enhance your organization’s cyber posture. Follow best practices for identity and access management, protective controls and architecture, and vulnerability and configuration management.
-
Increase organizational vigilance. Stay current on reporting on this threat. Subscribe to CISA’s mailing list and feeds to receive notifications when CISA releases information about a security topic or threat.
CISA, the FBI, and NSA encourage critical infrastructure organization leaders to review CISA Insights: Preparing for and Mitigating Cyber Threats for information on reducing cyber threats to their organization.
Click here for a PDF version of this report.
The list of flaws exploited by Russian hacking groups to gain an initial foothold, which the agencies said are “common but effective,” are below —
-
CVE-2018-13379 (FortiGate VPNs)
-
CVE-2019-1653 (Cisco router)
-
CVE-2019-2725 (Oracle WebLogic Server)
-
CVE-2019-7609 (Kibana)
-
CVE-2019-9670 (Zimbra software)
-
CVE-2019-10149 (Exim Simple Mail Transfer Protocol)
-
CVE-2019-11510 (Pulse Secure)
-
CVE-2019-19781 (Citrix)
-
CVE-2020-0688 (Microsoft Exchange)
-
CVE-2020-4006 (VMWare)
-
CVE-2020-5902 (F5 Big-IP)
-
CVE-2020-14882 (Oracle WebLogic)
-
CVE-2021-26855 (Microsoft Exchange, exploited frequently alongside CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065)
Other recommended best practices are as follows —
-
Implement robust log collection and retention
-
Require accounts to have strong passwords
-
Enable strong spam filters to prevent phishing emails from reaching end-users
-
Implement rigorous configuration management programs
-
Disable all unnecessary ports and protocols
-
Ensure OT hardware is in read-only mode
Specific enterprise techniques are documented at MITRE and CISA encourages review by cybersecurity professionals and related organizations as soon as possible.
Just a few of the specific attack and discovery related techniques documented at MITRE include the following:
T1548 |
Abuse Elevation Control Mechanism |
Adversaries may circumvent mechanisms designed to control elevate privileges to gain higher-level permissions. Most modern systems contain native elevation control mechanisms that are intended to limit privileges that a user can perform on a machine. Authorization has to be granted to specific users in order to perform tasks that can be considered of higher risk. An adversary can perform several methods to take advantage of built-in control mechanisms in order to escalate privileges on a system. |
|
T1134 |
Access Token Manipulation |
Adversaries may modify access tokens to operate under a different user or system security context to perform actions and bypass access controls. Windows uses access tokens to determine the ownership of a running process. A user can manipulate access tokens to make a running process appear as though it is the child of a different process or belongs to someone other than the user that started the process. When this occurs, the process also takes on the security context associated with the new token. |
|
T1531 |
Account Access Removal |
Adversaries may interrupt availability of system and network resources by inhibiting access to accounts utilized by legitimate users. Accounts may be deleted, locked, or manipulated (ex: changed credentials) to remove access to accounts. |
|
CISA, the FBI, and NSA encourage the cybersecurity community—especially critical infrastructure network defenders—to adopt a heightened state of awareness, conduct proactive threat hunting, and implement the mitigations identified in the joint CSA. CISA recommends network defenders review CISA’s Russia Cyber Threat Overview and Advisories page for more information on Russian state-sponsored malicious cyber activity. CISA recommends critical infrastructure leaders review CISA Insights: Preparing For and Mitigating Potential Cyber Threats for steps to proactively strengthen their organization’s operational resiliency against sophisticated threat actors, including nation-states and their proxies.
Rewards for Justice Program
If you have information on state-sponsored Russian cyber operations targeting U.S. critical infrastructure, contact the Department of State’s Rewards for Justice Program. You may be eligible for a reward of up to $10 million, which DOS is offering for information leading to the identification or location of any person who, while acting under the direction or control of a foreign government, participates in malicious cyber activity against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act (CFAA). Contact +1-202-702-7843 on WhatsApp, Signal, or Telegram, or send information via the Rewards for Justice secure Tor-based tips line located on the Dark Web. For more details refer to rewardsforjustice.net/malicious_cyber_activity.
Caveats
The information you have accessed or received is being provided “as is” for informational purposes only. CISA, the FBI, and NSA do not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply endorsement, recommendation, or favoring by CISA, the FBI, or NSA.